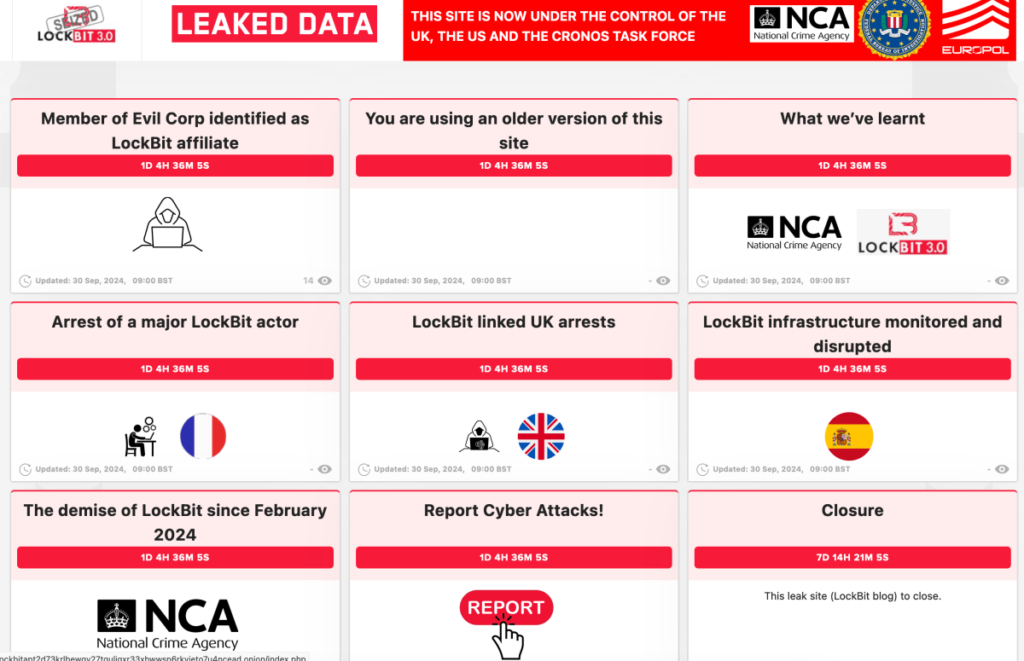
The UK's National Crime Agency has announced that it has linked a long-standing affiliate of the LockBit ransomware group to Evil Corp, a notorious Russian-backed cybercriminal organization with ties to the Russian government.
The NCA announced on Tuesday that it had revealed the true identity of Russian national Aleksandr Ryzhenkov of a Rockbit affiliate known as “Beverly”. British authorities believe he is Evil Corporation's “second-in-command.”
This is the latest effort by UK and international law enforcement agencies, dubbed 'Operation Kronos', to link LockBit, once one of the most prolific Russian ransomware gangs, with Russian links. It aims to disrupt the activities of Evil Corp, one of the top known Russian cybercrime groups. government. Authorities on Tuesday presented further evidence of overlap between two Russian cybercriminal groups, including the temporary reactivation of a dark web leak site from LockBit, a notorious ransomware group that authorities had previously seized.
According to the NCA's latest findings, Ryzhenkov is a close friend of Maxim Yakubets, the founder and leader of Evil Corp, who was indicted by the US government in 2019 for allegedly being involved in the development and distribution of Dridex malware. Yakubets was previously accused of providing “direct aid” to the Russian government.
As a result, Britain, along with US and Australian authorities, imposed sanctions on Ryzhenkov, effectively making it illegal for anyone with ties to those countries to do business with him, including paying ransoms.
In a press conference attended by TechCrunch ahead of Tuesday's announcement, the NCA said that while most of the Russian hackers it is tracking are financially motivated, Evil Corp maintains a “privileged” relationship with the Russian state and is a member of NATO. He said he was often tasked with carrying out cyber attacks on behalf of countries. of the Russian government.
Ryzhenkov, who the NCA describes as Yakubets's “right-hand man,” became affiliated with Rockbit in 2022 and went on to target at least 60 victims since then, authorities said.
The NCA also identified Maxim's father, Viktor Yakuvets. Maksim's father-in-law, former Russian intelligence official Eduard Bendersky, is key to Evil Corps' operations, with the latter being a “key enabler” of the gang's relationship with Russian intelligence. Yakubets and Bendersky were also sanctioned.
Gavin Webb, senior investigator for Operation Kronos, told reporters: “Rockbit has made it clear that they have never worked with Evil Corps, and we have made it very clear that they are. I was able to show that.”
The NCA also announced on Tuesday that a number of further arrests had been made in its ongoing efforts aimed at thwarting the prolific LockBit ransomware gang. British authorities have arrested two people in the UK believed to be connected to Rockbit-related companies on suspicion of computer hacking and money laundering crimes. A suspected LockBit developer was also arrested in France, and Spanish police detained one of the main proponents of the LockBit infrastructure and seized nine servers used by the group.
This action by Operation Kronos is the latest move in an ongoing cat-and-mouse game between international cyber authorities and Rockbit.
The long-running battle between the two sides became public in February, when an international law enforcement coalition led by the NCA and FBI announced it had breached LockBit's official website. In this multi-year operation, government agencies exploited vulnerabilities in Rockbit's public websites to compromise Rockbit's infrastructure, including dark web leak sites used by gangs to list and blackmail victims. Occupied.
In February, authorities also announced the arrest of two suspected Rockbit members in Ukraine and Poland and the seizure of more than 200 cryptocurrency wallets belonging to Russia-linked hackers.
A few days after the operation was announced, LockBit returned to the dark web with a new leak site and new victims.
Operation Kronos was carried out again in May and revealed new charges against Dmitry Khoroshev, a Russian national suspected of being involved as the creator, developer and administrator of Rockbit.
The NCA said LockBit remains active, but the actions taken so far have had a significant impact on ransomware activity. The NCA said the number of Rockbit-related organizations has fallen from around 200 to 70 since May, and the organization remains active by posting new victims on dark web leak sites. , but added that the majority are repeat victims or false allegations. .
The agency said its investigation into the LockBit ransomware also revealed new details about the gang's source code and how it operates. Authorities said Rockbit's code was written in such a way that it would not delete a victim's data, even if the victim demanded a ransom. The NCA said this detail was not known to Rockbit affiliates.