A broken iPhone was spotted during COP28 held in Dubai, United Arab Emirates on November 30, 2023. Image credits: Beata Zawrzel/NurPhoto (via Getty Images)
In 2019, Apple announced that it would start sending some security researchers a “special” version of the iPhone designed to use to find vulnerabilities, and then report them to Apple so that the company could identify the vulnerabilities. I made it possible to fix it. In 2020, the company began shipping devices designed to disable some security features to help researchers find bugs in iOS.
Before these devices existed, there existed a loosely organized group of hackers and security researchers known as “jailbreakers” who were dedicated to lifting the restrictions that Apple had placed on the iPhone. was doing. The term comes from the concept of breaking through Apple's security restrictions (called “prisons”) on the iPhone.
The purpose of jailbreakers is to have fun bypassing restrictions such as sideloading apps that are not included in the official App Store, and in the past, just to change the iPhone background before the feature is enabled. There was also a time when I was
Despite these seemingly innocuous goals, Apple has been at war with jailbreakers for years, discouraging people from disabling iPhone security features. There's still at least one Apple support page that refers to jailbreaks as “unauthorized changes” to iOS.
These days, Apple seems to embrace the term jailbreak by using it in the official documentation for its security research equipment. According to a photo posted on X (formerly Twitter) By security researcher Gergely Kalman.
“We've made it easy to run existing tools on security investigation devices. When you sideload tools through the cryptex subsystem, they run with platform privileges and the necessary privileges,” the description says. Masu. “This allows us to keep the systems under investigation in the same state as our customers while keeping the remaining security policies in effect and providing the flexibility of jailbroken devices.”

iPhone security research device with stickers and instructions. Image credits: Gergely Kalman
Kalman attached a photo of the box containing the iPhone security research device, a page of instructions for researchers, and three stickers he said were inside the box.
“Sorry for the lack of an unboxing video, but this is the Apple Security Research Device with accessories,” Kallman wrote in a post published Tuesday.
It's unclear how many of these security research devices actually exist, and there are few photos widely distributed online.
Apple spokesperson Scott Radcliffe said in a comment that TechCrunch asked how many of these devices Apple has shipped and whether the program has led to an increase in the number of vulnerabilities reported to the company. did not respond to the request.
Kalman told TechCrunch that his security research device is “identical” to the iPhone 14 Pro. The only difference, he added, is the words “Security Investigation Device” and Apple's phone number at the bottom of the locked screen, presumably to report it if it's lost.
Separately, Kalman said the box has a special tag that says “Do not remove” and “Property of Apple Inc.” and a serial number, which Apple has posted on its website. It is said that it is listed. Kallman said a sign on the side of the phone read: “Property of Apple. Confidential and Proprietary. Call +1 877 595 1125.”
Prior to Kallman's post on Tuesday, there appeared to be only one blog post featuring a photo of a security research device that was released in 2022.
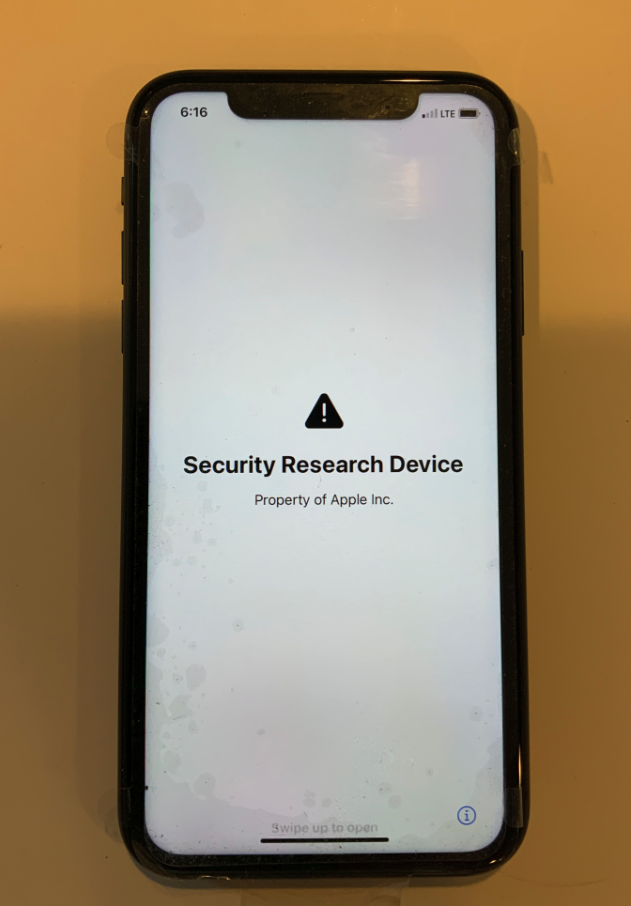
iPhone security research equipment. Image credits: Hoyt LLC
The launch of the Security Research Device program was, at least in part, a response to the proliferation of iPhone prototypes (technically known as “development fusion” devices) that were being bought and sold on underground markets by hackers and collectors.
These “fusion” devices are inherently devices that have not gone through the full production process, or have previously been used internally at Apple to test functionality, and are not intended to end up in the hands of consumers. It's not an iPhone. As a result, these devices lack most of the typical security features and limitations found on regular iPhones. This is what makes it especially attractive to security researchers. These devices make it easier for hackers to find bugs in the most heavily protected code of his iPhone.
This is why these devices cost thousands of dollars, and why Apple is cracking down on this gray market in addition to offering alternative security investigation devices.