KTrust, a Tel Aviv-based security startup, takes a different approach to Kubernetes security than many competitors in the space. KTrust takes a more proactive approach than just scanning Kubernetes clusters and their configurations for known vulnerabilities. Deploy automated systems to attempt to hack into systems. This allows security teams to focus on the actual attack path, not just the long list of potential security vulnerabilities. So KTrust is essentially a read-in-the-box team. However, research firm Gartner prefers to call it Continuous Threat Exposure Management (CTEM).
Ktrust today came out of stealth and announced a $5.4 million seed funding round led by AWZ Ventures.
Like many Israeli security companies, the management team comes to the company with a wealth of experience. CEO Nadav Toledo previously served as a colonel in the Israel Defense Forces' 8200 Intelligence Unit, where he spent 25 years before founding KTrust. CTO Nadav Aharon-Nov Previously, he served as his CTO for the intelligence and defense company R-MOR. COO Sigalit Shavit previously served as global CIO of publicly traded CyberArk. CBO Snit Mazilik complements the group with extensive business experience, including as CEO of Shanghai-based fashion wholesaler Must Garment Group and managing partner of real estate investment company NOI Ventures. This is an eclectic group of founders, but as Toledo told me, “Everyone brings a different perspective to the board, and it's just a great team.”
As a group, Toledo, Aharon-Nov, and Mazilik began brainstorming different ideas for a security startup. That the team ended up with his Kubernetes is not necessarily surprising, given that Kubernetes is still a rapidly growing ecosystem that many traditional companies are just beginning to adopt.
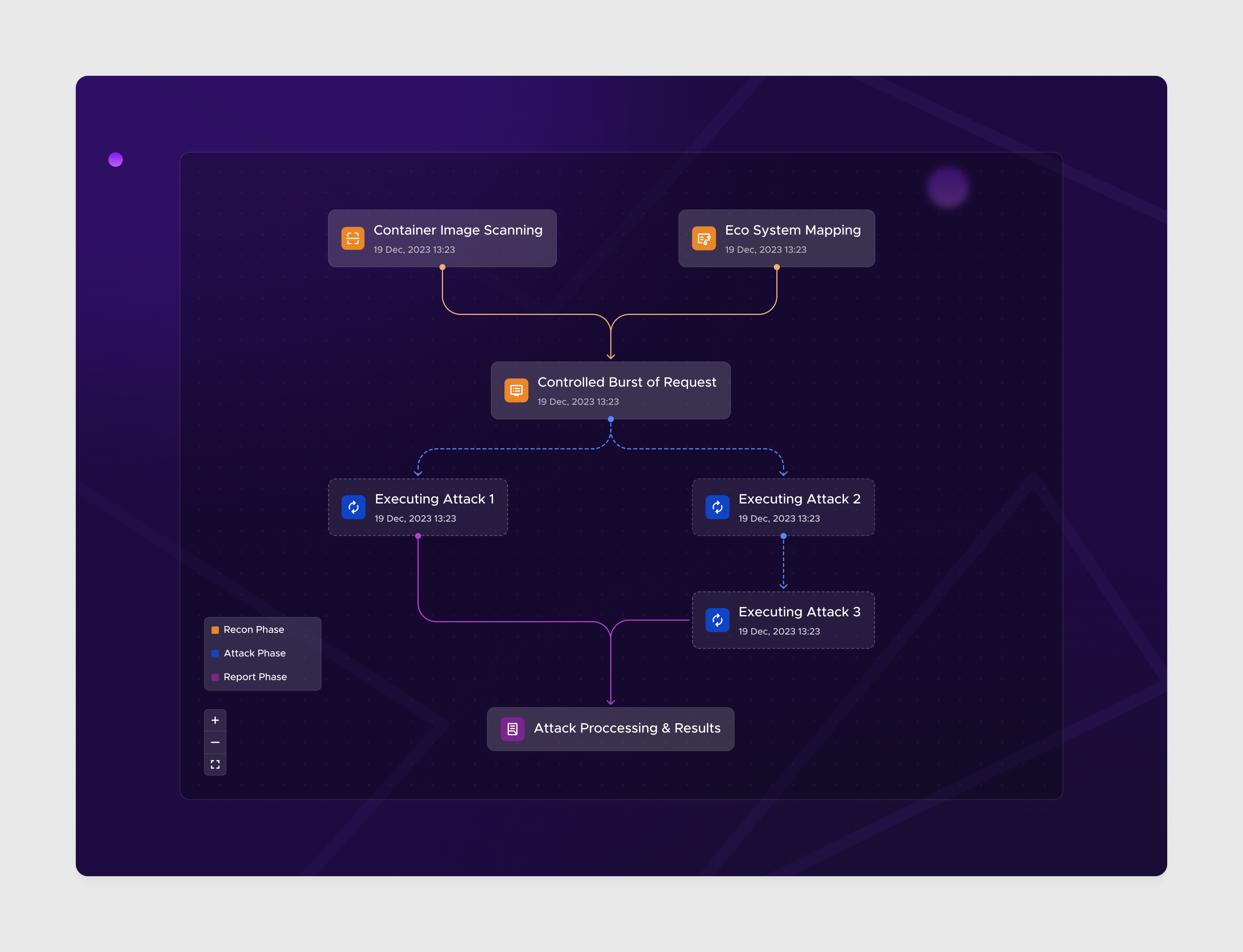
Image credits: K Trust
“Kubernetes is very complex and very dynamic. We visited organizations and talked to DevOps teams and CISOs. […] We've seen DevOps teams struggle. I've also seen DevSecOps teams struggle because they want him to be the Kubernetes expert, meaning he's in charge of configuring Kubernetes, and on the other hand he wants him to be the security expert. ” Toledo told me.
The team noted that most Kubernetes security solutions take what he calls a “passive scanner approach” that focuses on performing static code analysis. But that results in a lot of alerts, so someone needs to convert these into a work plan. The idea behind KTrust is to take a completely different approach by using automated red team algorithms that proactively explore attack vectors and identify points of compromise in Kubernetes-based systems. . KTrust takes a customer's Kubernetes infrastructure configuration and clones them into a secure sandbox that algorithms can attack.

Image credits: K Trust
This algorithm mimics a real attacker. “By doing this, we find the actual attack vector to exploit and avoid having to retrieve a list of hundreds of unconnected items. We present verified exploits to DevSecOps, but this is a real validation because it was an actual attack,” Toledo explained. While working with a recent client, he said his passive scanners discovered more than 500 vulnerabilities, but by using KTrust's agent-based systems, the team was able to convert this into a real attack. He noted that he was able to narrow it down to about 12 passes.
KTrust allows security teams to see exactly how algorithms attack their systems. When it comes to mitigation, the service provides users with manual mitigation recommendations and can often automate these steps as well.
It is worth noting that the company employs a group of security experts dedicated to discovering new attack vectors. The team has already submitted a number of his CVEs (Common Vulnerabilities and Exposures) for Kubernetes and Argo CD.
“Our investment in KTrust demonstrates our confidence in KTrust’s distinctive Kubernetes security solutions, which meet critical market demands. To ensure deployment, we scale to power DevSecOps globally,” said Yaron Ashkenazi, Managing Partner at AWZ Ventures.



