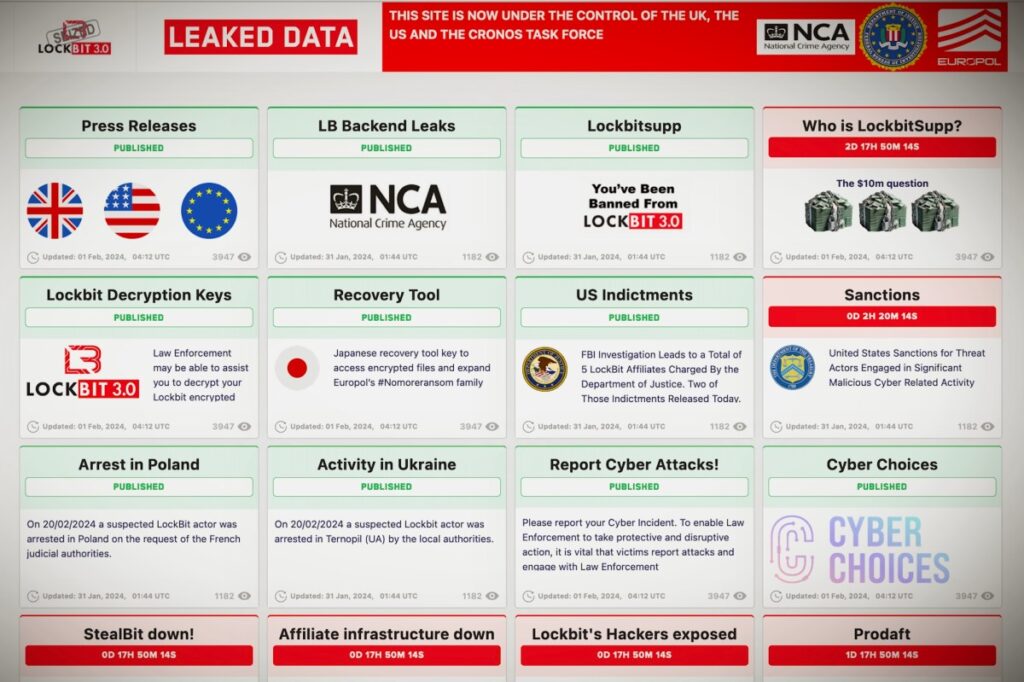
The US government has sanctioned two key members of the Russian-speaking hacking and extortion group Rockbit, who are accused of launching ransomware attacks against victims across the US and abroad.
The U.S. Treasury Department confirmed in a post on Tuesday that it is sanctioning two Russians, Artur Sungatov and Ivan Gennadyevich Kondratyev.
Mr. Sungatov and Mr. Kondratyev were separately indicted by U.S. prosecutors on Tuesday for their alleged involvement in Rockbit.
Mr. Kondratyev is also accused of involvement in the REvil, RansomEXX, and Avaddon ransomware gangs.
“The United States will not tolerate attempts to rob and steal from our people and institutions,” Wally Adeyemo, deputy US Treasury secretary, said in a statement. “We will continue our whole-of-government approach to defending against malicious cyber activity and will use all available tools to hold accountable the actors who enable these threats.”
The newly imposed sanctions mean it is now illegal for U.S. companies and individuals to make payments or transactions with those named as sanctioned parties, which typically means that U.S. victims are vulnerable to hackers. This is a tactic used to discourage people from paying the ransom.
By sanctioning the individuals behind cyberattacks, individual hackers benefit from ransomware, rather than targeting groups that can rebrand or rename to avoid sanctions. becomes more difficult.
If a company is caught violating U.S. sanctions laws, such as by paying money to sanctioned hackers, it can lead to hefty fines and criminal prosecution.
The sanctions were lifted hours after U.S. and British authorities announced a global enforcement operation aimed at disrupting Rockbit's infrastructure and operations. Authorities announced the seizure of Rockbit's infrastructure on the gang's own dark web leak site. The group previously used the site to publish stolen data of victims unless a ransom was paid.
U.S. prosecutors have accused LockBit operators of using ransomware in more than 2,000 cyberattacks on victims in the U.S. and around the world, paying about $120 million in ransoms since its founding in 2019. ing.
LockBit has credited hundreds of hacks over the years that affected the personal information of millions of individuals, including the California Department of Treasury, the British postal service Royal Mail, and the US dental insurance giant MCNA. I have praised it.
The US sanctions announced on Tuesday are the latest measures targeting the hackers behind LockBit and other prolific ransomware gangs.
In 2022, Mikhail Vasiliev, a dual citizen of Russia and Canada, was arrested on suspicion of launching multiple LockBit ransomware attacks. A year later, US authorities arrested Ruslan Magomedovich Astamirov on similar charges. Both suspects remain in custody awaiting trial.
The third suspect, Mikhail Pavlovich Matveev, a Russian national, was charged with involvement in several ransomware operations, including LockBit. Matveev, who remains at large, will be subject to U.S. sanctions in 2023, preventing American victims from paying ransoms to him or related ransomware groups such as Hive and Babak. The US government is also offering a $10 million reward for information leading to Matveyev's arrest.
In Tuesday's announcement, the U.S. government has not yet named the alleged mastermind of LockBit, nicknamed LockBitSupp. Law enforcement is expected to release more information about the suspected leader on Friday, including his whereabouts and details of a $10 million reward for information leading to his identification, according to LockBit, a now-seized dark web leak site. That's what it means.
Besides sanctions, the United States does not prohibit or restrict victims from paying ransoms, but the FBI has long advised victims not to pay ransoms to hackers for fear of perpetuating future cyberattacks. I've done it. Security researchers say ransomware victims who pay a ransom are more likely to be subject to further ransomware attacks.
Read more on TechCrunch: