This week, a wide-ranging law enforcement operation led by the UK's National Crime Agency took down LockBit, the notorious Russia-linked ransomware gang that has been wreaking havoc on businesses, hospitals and governments around the world for years.
The action brought down LockBit's leaked site, seized its servers, led to multiple arrests, and led to one of the most significant operations ever undertaken by the U.S. government against the ransomware group. Sanctions have been applied.
It's also arguably one of the most cutting-edge takedowns we've ever seen, with British authorities announcing the seizure of Rockbit's infrastructure on the group's own leak site. The site currently contains many details about the gang's inner workings, and promises that more information will be released. To come.
Here's what we've learned so far:
LockBit didn't delete victims' data – even if victims paid for it
It has long been suspected that paying a hacker's ransom demand is a gamble, with no guarantee that stolen data will be deleted. Some corporate victims have said that they “cannot guarantee” that their data will be erased.
LockBit removal confirmed this to be absolutely the case. The NCA revealed that some of the data found on LockBit's seized systems belonged to victims who paid ransoms to threat actors. This proves that even if the ransom is paid, there is no guarantee that the data will be deleted no matter what the criminals do. ” the NCA said in a statement.
Even ransomware gangs fail to patch vulnerabilities
Yes, even ransomware gangs are slow to patch software bugs.According to the Malware Research Group vx-underground LockBitSupp, the alleged leader of Operation LockBit, said law enforcement agencies used known vulnerabilities in the popular web coding language PHP to hack into the ransomware operation's servers.
The vulnerability used to compromise the server is tracked as CVE-2023-3824, a remote execution flaw, and was patched in August 2023, with LockBit taking several steps to fix the bug. It took a month.
LockBitSupp's translated message to vx-underground reads, “The FBI fabricated a server via PHP. Backup servers without PHP are not accessible.” It was originally written in Russian.
Ransomware removal takes a long time
The dismantling of Rockvit, officially known as Operation Kronos, was years in the making, according to European law enforcement agency Europol. The agency said on Tuesday that the investigation into the notorious ransomware ring began nearly two years ago, in April 2022, at the request of French authorities.
Since then, Europol has confirmed that the European Cybercrime Center (EC3) has held more than 20 steering meetings and meetings to gain leads ahead of this week's raid, the final stage of the investigation. He said he held four one-week technical sprints.
LockBit hacked over 2,000 organizations
LockBit, which first entered the cybercrime scene in 2019, has long been known to be one of the most prolific ransomware gangs, if not the most prolific.
Tuesday's operation largely confirms that, and the U.S. Department of Justice now has the numbers to back it up. According to the Department of Justice, LockBit claimed more than 2,000 of his victims in the United States and around the world, and he received more than $120 million in ransom payments.
Sanctions targeting key LockBit members could impact other ransomware
One of the top Rockbit members indicted and sanctioned on Tuesday was Russian national Ivan Gennadyevich Kondratyev, who U.S. authorities allege is connected to other ransomware gangs. ing.
Kondratyev also has ties to REvil, RansomEXX and Avaddon, according to the US Treasury Department. While RansomEXX and his Avaddon are lesser-known variants, REvil is also a Russian-based ransomware variant that hacked US network monitoring giant Kaseya and paid a multi-million dollar ransom. became famous for
Mr. Kondratyev was also named the leader of a newly disclosed subgroup of Rockbit called the “National Dangerous Association.” Little is known about this Rockbit affiliate yet, but NCA has promised to reveal more details in the coming days.
The sanctions effectively prohibit Kondratiev's U.S.-based ransomware victims from paying the ransom he demands. Sanctions could make Mr. Kondratyev's life five times harder, given that he is involved in at least five different ransomware gangs.
British people have a good sense of humor
Some people (namely me, a British person) would argue that we already knew this, but the Rockbit sting incident showed that the British authorities have a sense of humour.
NCA didn't just mock LockBit by imitating the gang's dark web leak site for its own LockBit-related disclosures. We found various Easter eggs hidden on his LockBit site, which has now been confiscated. Our favorites are the various file names for images on the site, such as “oh dear.png,” “doesnt_look_good.png,” and “this_is_really_bad.png.”
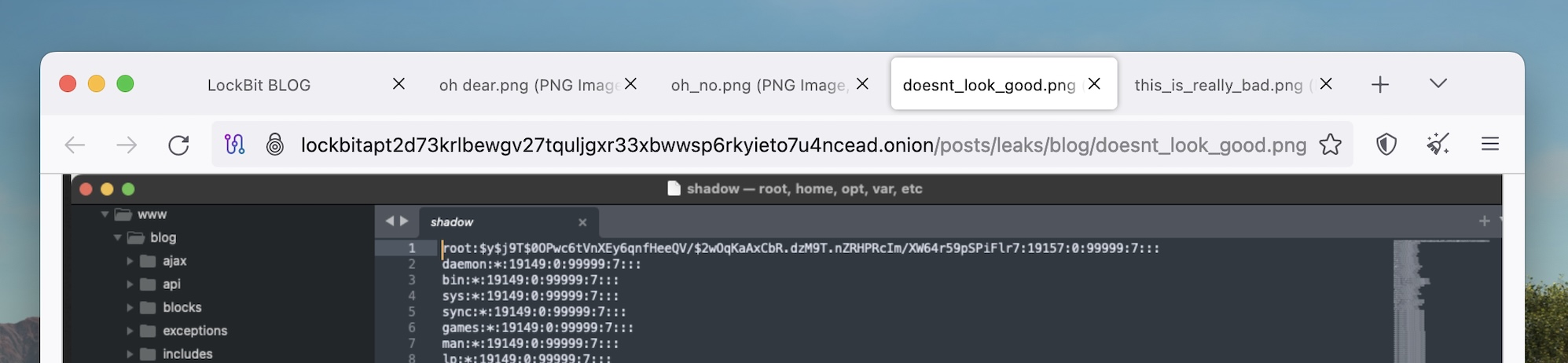
Image credits: tech crunch



