Google today announced significant changes to Chrome's Safe Browsing feature. This allows the service to work in real-time by checking your browsing habits against server-side lists without sharing them with Google.
Previously, Chrome downloaded a list of sites known to harbor malware, unwanted software, and phishing scams once or twice an hour. Going forward, Chrome will move to a system that sends the URL you're visiting to its servers, where it matches it against a rapidly updated list. The advantage of this is that it takes up to an hour to get an updated list. As Google points out, the average malicious site doesn't exist for more than 10 minutes.
The company claims this new server-side system can catch up to 25% more phishing attacks than using local lists. The size of these local lists has also grown, putting more strain on low-end machines and low-bandwidth connections.
Google is currently rolling out this new system to desktop and iOS users, with Android support expected later this month.
Share URL privately
Now, if all of this sounds a little familiar, it's probably because you're already familiar with Safe Browsing Enhanced Mode. This mode compares the URLs you're visiting against a real-time list online, but uses AI to block unlisted attacks, perform more in-depth file scanning, and protect you from malicious Chrome extensions. It also provides protection. However, enhanced mode has always been opt-in and will remain opt-in (even though Google started encouraging users to turn it on last year). Standard protected mode does not use these AI features.
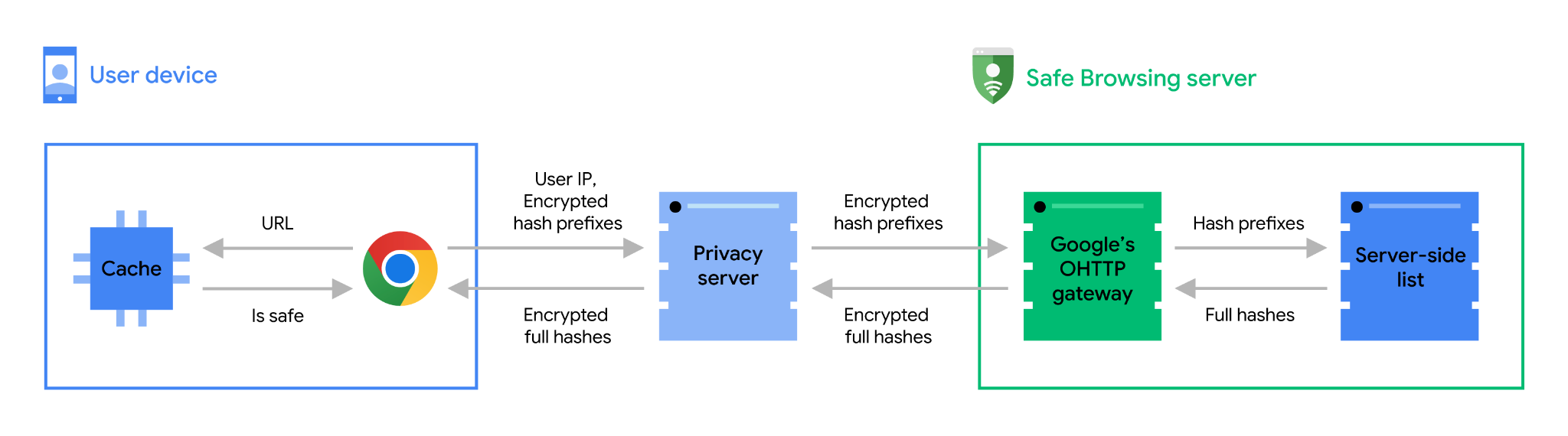
Google has gone to great lengths to explain how this system works in real time, without sharing your browsing data with the company. Google explains this process:
When you visit a site, Chrome first checks its cache to see if the site's address (URL) is already known to be safe (for more information, see Keeping it fast and reliable) section).
Real-time checking is necessary because the URL you visit may not be secure if it is not in the cache.
Chrome obfuscates URLs by converting them into a full 32-byte hash according to URL hashing guidance.
Chrome truncates the full hash to a 4-byte long hash prefix.
Chrome encrypts the hash prefix and sends it to a privacy server.
The privacy server forwards the encrypted hash prefix to the Safe Browsing server over a TLS connection, removing potential user identities and mixing the request with many other Chrome users.
The Safe Browsing server decrypts the hash prefix, checks it against a server-side database, and returns a complete hash of all unsafe URLs that match one of the hash prefixes sent by Chrome.
After receiving the full insecure hashes, Chrome checks them against the full hash of the URL you visited.
If a match is found, Chrome will display a warning.
Perhaps the most interesting part here is the privacy server. In fact, Google has partnered with his CDN and edge computing specialist Fastly to use Fastly's Oblivious HTTP Privacy Server. This server sits between Chrome and Safe Browsing and strips identifying information from browser requests.
Fastly built this system as a privacy service that sits between users and web applications, allowing metadata to be anonymized while exchanging data with the web application. Google emphasizes that these servers are independently run by Fastly (a cynic might look at this and say that even Google isn't confident that it won't snoop on your browsing data… ).
Thanks to all this, Google's Safe Browsing service will never know your IP address. Fastly, on the other hand, doesn't see these URLs because they're encrypted by your browser using a public/private key that Fastly doesn't have access to.



