New research has found that malicious hackers could take control of Ecovacs vacuum cleaners and lawnmower robots, using the devices' cameras and microphones to spy on their owners.
Security researchers Dennis Giese and Braelyn will be presenting their work on Ecovacs robots in detail at the Defcon hacking conference on Saturday. After analyzing several Ecovacs products, the researchers found several issues that could be exploited to hack the robots via Bluetooth and secretly turn on their microphones and cameras remotely.
“Their security was really, really, really, really bad,” Giese told TechCrunch in an interview before the talk.
The researchers said they contacted Ecovax to report the vulnerability but did not receive a response from the company, and they believe the vulnerability remains unpatched and could potentially be exploited by hackers.
Ecovacs did not respond to TechCrunch's request for comment.
The main problem, according to the researchers, is that a vulnerability in the ECOVACS robots could allow someone to connect to and take over them using their smartphone over Bluetooth from up to 450 feet away, and once a hacker has control of the device, they could connect to it remotely, since the robots themselves are connected to the internet over Wi-Fi.
“You send a payload, which takes a second, and it connects to the machine, so it can connect to a server on the internet, for example, and then you can remotely control the robot from there,” Giese says. “It can read Wi-Fi credentials, [saved room] “And maps. You can control the operation of the robot's Linux operating system, so you can access the camera, microphone, everything.”
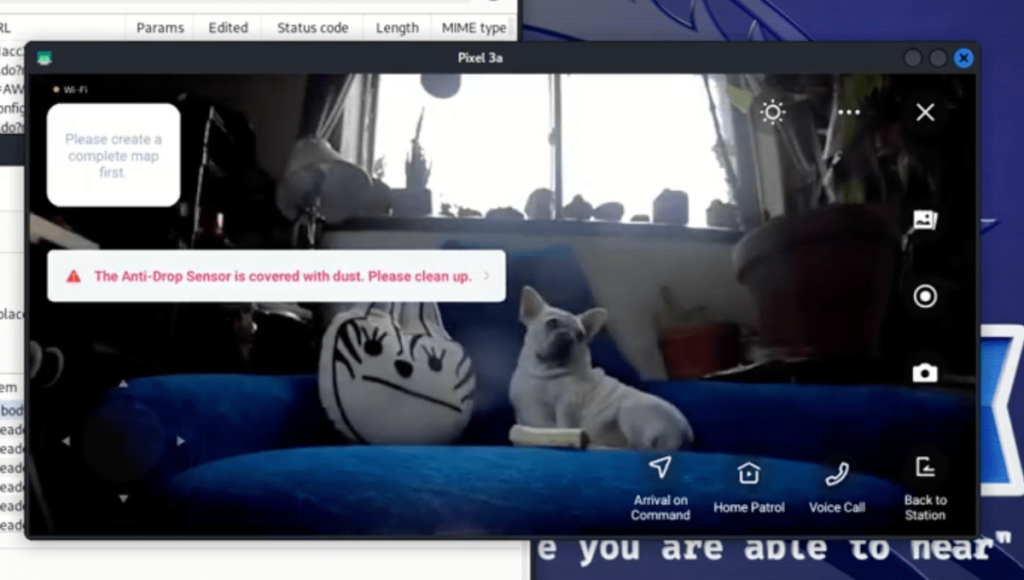
 A dog seen through a hacked Ecovacs device. Image courtesy of Dennis Guise and Braelyn (Courtesy) Image courtesy of Dennis Guise and Braelyn
A dog seen through a hacked Ecovacs device. Image courtesy of Dennis Guise and Braelyn (Courtesy) Image courtesy of Dennis Guise and Braelyn
Giese said that while lawnmower robots have Bluetooth enabled all the time, vacuum robots enable Bluetooth for 20 minutes when they're turned on and then once a day when they auto-reboot, making them a bit harder to hack.
Most of Ecovax's new robots are equipped with at least one camera and microphone, which could allow a hacker to turn a compromised robot into a spy if they gain control of it. The robots have no hardware lights or other indicators that would alert nearby people that a camera or microphone is on, according to the researchers.
Some models theoretically play an audio file every five minutes to indicate that the camera is on, but Giese said a hacker could easily delete that file to remain stealthy.
“Basically it just deletes the file or overwrites it with a blank file, so if you access the camera remotely it won't play the alert,” Giese said.
Aside from the risk of hacking, Giese and Braelin said they had found other issues with Ecovax's equipment.
The problem is that the data stored on the robot remains on Ecovacs' cloud servers even after the user's account is deleted, and the authentication token also remains in the cloud, meaning that someone could access the robot even after the account is deleted, potentially allowing them to spy on people who may have bought a used robot. Also, the lawnmower robot has an anti-theft mechanism that forces you to enter a PIN code when you pick up the robot, but that PIN code is stored in plain text on the lawnmower, making it easy for a hacker to find and use it.
The researchers said that once an Ecovax robot is compromised, other Ecovax robots could also be hacked if the device is within range of those robots.
Giese and Braelyn said they analyzed the Ecovacs Deebot 900 Series, Ecovacs Deebot N8/T8, Ecovacs Deebot N9/T9, Ecovacs Deebot N10/T10, Ecovacs Deebot X1, Ecovacs Deebot T20, Ecovacs Deebot X2, Ecovacs Goat G1, Ecovacs Spybot Airbot Z1, Ecovacs Airbot AVA, and Ecovacs Airbot ANDY.