Days after the Port of Seattle announced a “possible” cyberattack on its systems, Seattle-Tacoma International Airport remains largely offline, causing confusion among travelers and a warning against neglecting security. Ask me why I know.
The recent hacking outage, fortunately, did not result in any planes crashing or air traffic controllers double-booking runways. These federally run resources are fairly tightly controlled.
Rather than being a catastrophe, the situation we find ourselves in now is a lesson in why we have rules about where we dump our eggs, even for the foreseeable future, as authorities have not provided a timeline for recovery.
I found this out on Sunday when I tried to reserve my place in the security line with SEA Spot Saver. I hesitate to even mention this because no one seems to know about this miraculous service. The fact that SEA Spot Saver is offline and throws errors that you don't have to be a system administrator to notice means there's something more serious.
If I were a good reporter and had read my publication over the weekend, I would have seen that this was the result of, among other things, a complete rigging of the entire user-facing DNS configuration of the Port’s web architecture. (The Spot Saver site is still offline, but the functionality has been reinstated by Clear for now.)
Luckily, I didn't have any checked luggage (I'd been officially warned) and security was lax because a jackknifed big tractor-trailer was blocking all southbound traffic on I-5, presumably.
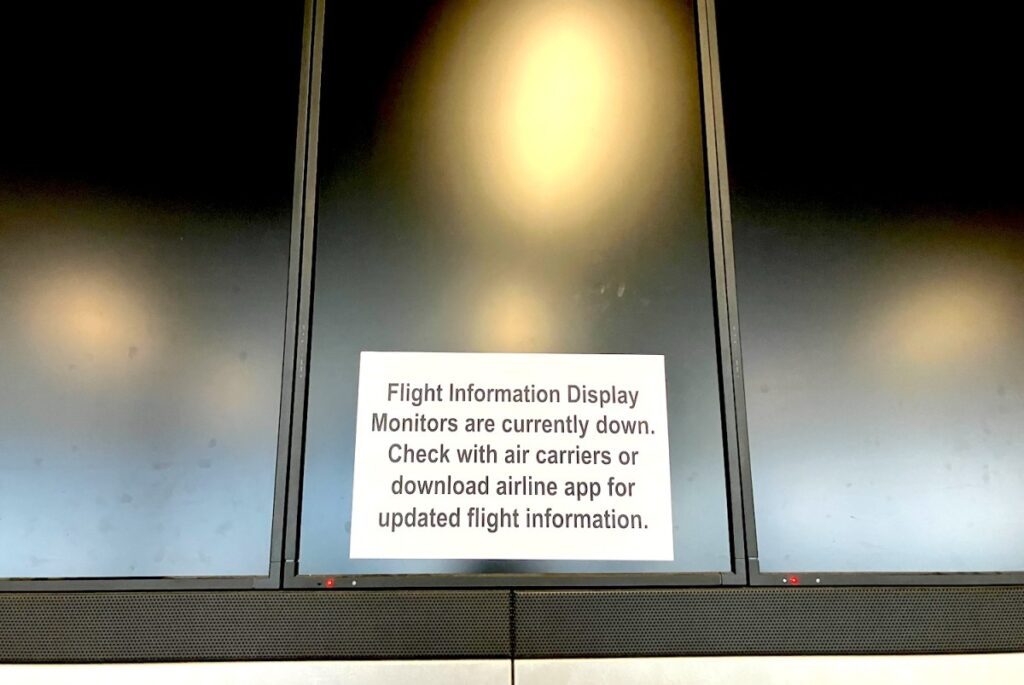
At the airport, the big screens I normally hover over to check my flight were eerily dark, but given the never-ending construction at Seattle-Tacoma International Airport, I figured this was due to electrical work.
It was only at the S Gates that the scope of the problem became apparent: Every screen in that area was dark, including the television above the waiting room, the multi-display array directing travelers to their gates, the gate agent's monitor and the gate information display itself.
There was a gate indication on the boarding pass, but I wasn't sure if it was the correct gate, so I asked the attendant, who confirmed it and I asked about the hack.
“It sure is a bit… show-like,” they agreed, but politely left out the same part I'd said. All of the airport systems shared by multiple airlines were down. Baggage handling was awful, they said. They ignored their own rules about baggage size (don't tell anyone!) and didn't bother to round up “volunteers” to check bags at the gate and expedite boarding. Communication between airlines was difficult.
I was told that the gate desks were mostly offline as it was an officially shared system between Alaska Airlines, Delta, and all other passengers coming into the S-gates. No one could see the flight number, boarding group, or delay (30 minutes in the case of my flight) except at the PA. At the PA, it was very competitive as you constantly had to repeat the current gate number. One of the nearby gates had a paper sign announcing the last flight that had departed, but it was obviously several hours ago.

The check-in tablet worked but was “limited,” and no flight or seat changes were made. (I hopefully suggested I might have been upgraded to first class, only to be shooed away.)
In a world where digital infrastructure is crashing, sometimes those who stick with analog resources seem smart, not old-fashioned. Not today. While we waited, every few minutes someone would come up to the gate with a paper ticket and tell us this was where we were leaving from. Some were lucky to be told they were just a few steps away, while one unlucky person was redirected all the way to the N Gate, which is, you guessed it, the exact opposite of the S Gate.
The solution, suggested by gate agents and paper signs tacked to blank displays, was to use an app, but problems like this week are precisely why no one can really trust the “app,” because it's just as susceptible to hacker attacks as the ports themselves.
What's surprising is that the hackers were able to take down so many systems at once. There's no need to think of baggage handling, gate handling, and security as completely siloed and inseparable. This is an airport, not a nuclear power plant.
But at the same time, it seems odd that there is such a lack of resilience in the systems. Sure, the airport intranet might go down, but would the entire public-facing website go down? And baggage routing and gate updates? Is it all on the same network? We've understood the need to split up critical systems for centuries, and we've built that into our power and network infrastructure so that one person running two hairdryers at the same time doesn't take down an entire neighborhood.
I'm not complaining because it was an inconvenience — to be honest, this trip to the airport was no better or worse than any other trip I've taken — but I saw countless people getting into trouble due to a government IT infrastructure that is poorly secured and probably woefully understaffed.
When the federal government talks about upgrading critical infrastructure, this is what they’re talking about. Yes, it’s the 80s-era computers running COBOL that control our traffic lights, dams, and missile silos. But it’s events like this, more than the CrowdStrike disaster, that really highlight the weaknesses and vulnerabilities of our local and national systems: a worryingly large attack surface with relatively few resources dedicated to maintaining it.
Many potential attackers have been deterred by the fact that they are less valuable targets than financial institutions or data brokers, but that is changing. For example, ransomware has proven to be profitable and easy to automate, and AI (which was bound to come along at some point) is giving a strong boost to credential theft via spear phishing attacks. This means that unlikely targets for ransom (schools, libraries) will only become more prevalent, but these attacks are just as preventable as the private sector targets that have been expected for decades.
People traveling through Seattle-Tacoma International Airport should allow a little more time for waiting at the airport and installing related apps. State and city officials are doing their best to keep everyone informed on this crisis page.