In his quest to turn the simple, functional Twitter app into X, an everything app that doesn't do anything well, Elon Musk launched voice and video calling in X last week — and this new feature. is turned on by default and leaked Your IP address can be known to anyone you talk to, making it very confusing to understand how to limit who can call you To do.
X's official news account posted on Wednesday, Announcing new features: “Voice and video calling is now available to everyone on X! Who will you call first?” wrote X.
We looked at X's official help center page, analyzed how the calling feature works, and ran tests on the feature to understand the risks associated with it.
Although a person's IP address is not very sensitive, these online identifiers can be used to infer location and can be linked to a person's online activities, which can be dangerous for high-risk users. .
First, the voice and video calling functionality is located within the Messages portion of the X app, with a phone icon in the top right corner on both iOS and Android.
Screenshot of X audio and video calling features on iOS. Image credit: TechCrunch
Screenshot of X audio and video calling features on Android. Image credit: TechCrunch
Calling is enabled by default in X apps. Please note that you can only make and receive calls in the X app, not in the browser yet.
By default, calls are peer-to-peer. This means that the two people on the call share each other's IP addresses, as the call connects directly to their own devices. As we reported in November, this happens by design in most messaging and calling apps, including FaceTime, Facebook Messenger, Telegram, Signal, and WhatsApp.
in Official help centerMr. X said calls are routed peer-to-peer between users in such a way that IP addresses “may be visible to the other party.”
If you want to hide your IP address, turn on the “Enhanced call privacy” toggle in X's Messages settings. When this setting is turned on, X says that calls will be “relayed through the X infrastructure, masking her IP address for callers who have this setting enabled.”
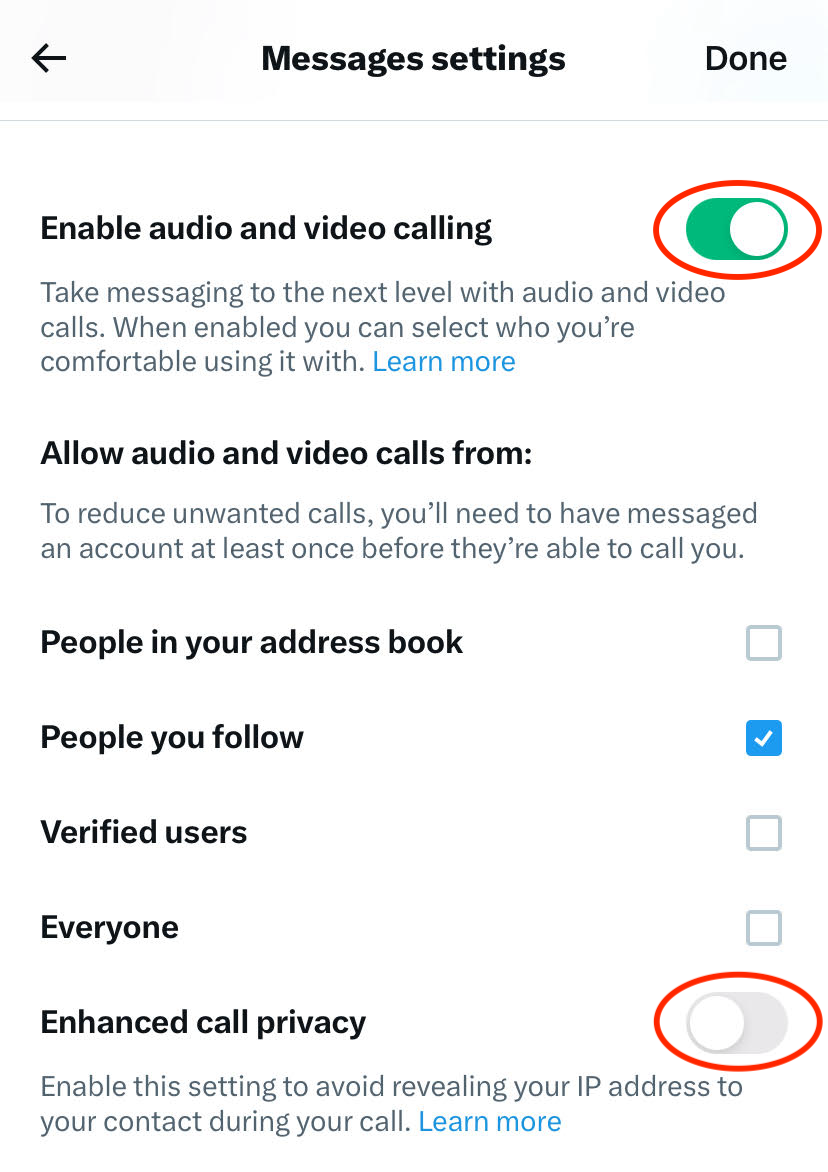
Screenshot of settings for audio and video calling features in X for iOS. Image credit: TechCrunch
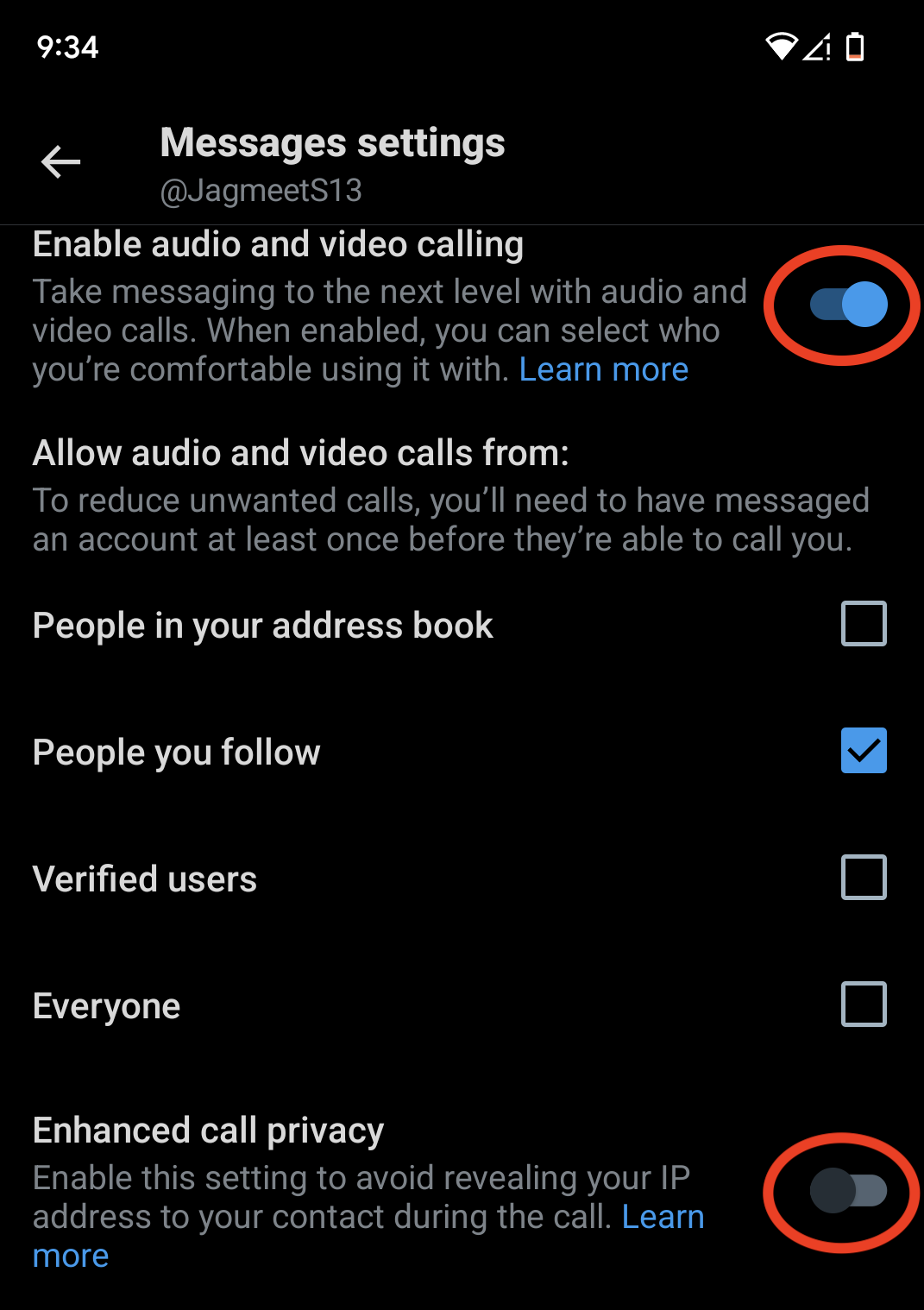
Screenshot of settings for audio and video calling features in X for Android. Image credit: TechCrunch
X doesn't mention encryption at all on its official help center page, so it's likely that the calls are not end-to-end encrypted and Twitter could potentially eavesdrop on the conversation. End-to-end encryption app, Signal or WhatsApp — Prevents anyone other than the caller and recipient from eavesdropping, including WhatsApp and Signal.
We asked X's press email if it has end-to-end encryption. The only response we got was “I'm busy right now, please check back later”, which is X's default automatic response to media inquiries. I sent an email to Joe Benarroch, a spokesperson for X, but did not receive a response.
Because of these privacy risks, we recommend that you turn off calling functionality completely.
If you want to use this calling feature, it's important to understand who can and can call you. Depending on your setup, it can get very confusing and complicated.
The default setting (as seen above) is “People I follow,” but you can also change it to “People in my address book” if you've shared your contacts with X. “Authenticated User”: Anyone who has paid for X can call you. If you want to receive spam calls from Rand, send them to everyone.
TechCrunch decided to test a few different scenarios using two X accounts: a newly created test account and a real account that has been around for many years. Using the open source network analysis tool Burp Suite, we were able to see the network traffic flowing into and out of the X app.
Here are the results (at the time of writing):
If both accounts follow each other, neither account will have a phone icon and neither will be able to make a call. When the test account sends a DM to the real account, the message is received, but neither account shows a phone icon. Once the real account accepts the DM, the test account can call the real account. If no one comes out, only her IP of the caller of the test account will be published. When the test account initiates a call and the real account answers (the real account's IP address is exposed, so both sets of IP addresses are exposed), the test account allows incoming “Follow” calls. It cannot be called back because it is set to . only. Once the real account follows back the test account, both will be able to contact each other.
Network analysis shows that X built the calling feature using Periscope, Twitter's live streaming service and app, which was discontinued in 2021. Because X's calls use his Periscope, network analysis shows that the X app is making the calls as if they were Twitter/X live broadcasts. Even if you can't hear the call.
Ultimately, it's your choice whether or not to use X calls. Since you can't do anything, you may be exposed to calls from people you probably don't want to receive calls, and your privacy may be violated. Alternatively, you can decipher X's settings to limit who can call you. Or you can just turn off this feature completely and you won't have to worry about anything.
Carly Page and Jagmeet Singh contributed reporting.



